Remote Access VPN Guide
For many companies, setting up a remote access VPN is the only viable solution in order to establish a remote workforce. The reason is simple: they already own the equipment necessary to set up a VPN.
All next-gen firewalls have the capability to provide remote access. The real concern here is not about access, but about following industry best practices in order to properly secure VPNs. In this article, we will review what a remote access VPN is, important design considerations, and how to enhance user visibility.
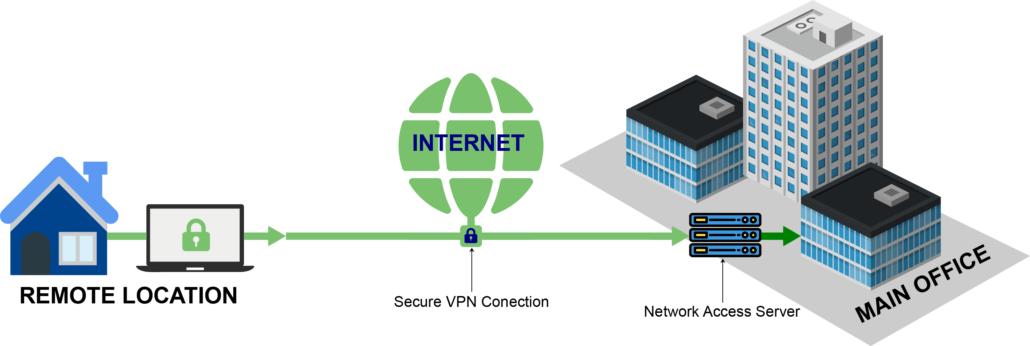
What is Remote Access VPN?
A remote access VPN (Virtual Private Network) enables users to access enterprise applications that reside in the corporate data center or headquarters remotely. All the traffic is encrypted, making sure that communication is not compromised. Think of it as a virtual cable that is connecting the remote user directly to the data center.
Building Remote Access
When building remote access there are many design considerations. Below you will find a list of eight items all network and security teams should investigate prior to setting up a VPN.
- Update your firewalls
- Depending on your firewall software release you might be limited to lower encryption and hashing algorithms, which would make your VPNs less safe. Most importantly, the enterprise could be exposed to known vulnerabilities.
- How many users does your device support?
- VPN support is dependent on hardware. The more CPU, Memory, Hardware enhancements, etc., the more users can be supported. Make sure to check your hardware model and how many concurrent sessions are allowed.
- User authentication
- Firewalls and VPN concentrators can authenticate users via shared passwords, locally created accounts and centrally authenticated. The most scalable and secure authentication method is the central type, which can leverage radius and active directory.
- Differentiated access
- Configure access policy depending on assigned user roles
- Use strong encryptions and hashing for data privacy and integrity
- The use of strong algorithms like AES-256. Sha 512, and ECDH
- Device resiliency
- Set up multiple VPN gateways to service users
- Type of tunnel
- Split tunneling is when remote users can access secured and unsecured networks when connected to a VPN. This creates the possibility that malicious users can use the remote user’s link to the corporate network to access resources on the corporate LAN through the authenticated connection. Full Tunnel (recommended) routes and encrypts all request through the VPN regardless of where the services is hosted.
- Prevent man-in-the-middle attacks
- Make sure your VPN has a certificate. This helps validate that users are connecting to the correct VPN gateway and not a malicious site.
Enhancing Remote User Visibility
Enhancing remote end-user visibility is very important. Cisco has reported that 82% of mobile workers admit to not always using the VPN. As a cloud-delivered service, Umbrella provides the visibility needed to protect internet access across all network devices, office locations, and roaming users. Internet activity is logged and categorized by the type of security threat or web content, and whether it was blocked or allowed.
Cisco Umbrella includes the following security services:
- Prevents malware, ransomware or phishing attempts from malicious or fraudulent websites
- Prevents both web and non-web Botnet Command & Control call-backs from systems that are already compromised
- Protects roaming users and devices, regardless of their location and without the need to be connected to an office network or VPN
- In-built integration with Cisco AMP and anti-virus engines provides file inspection capabilities
- Enhanced visibility of real-time security activity to identify compromised systems and targeted attacks
- Enforces and complies with the organization’s acceptable use policy, using over 60 in-built content categories, as well as custom-defined white and blacklists.
The sudden accelerated shift to remote working for many organizations in response to COVID-19 can introduce new risks and vulnerabilities, especially at critical connection points. Call us today to learn additional ways you can keep your organization secure. Whether you have questions on remote access VPN best practices or need help with implementation, we are here for you.